?What is Masscan
Masscan is a network port scanner, similar in many ways to the well-known Nmap command. The goal of Masscan, however, is to enable security researchers to run port scans on large swathes of the Internet as quickly as possible.
Port scanners are among the most important tools in a researcher’s toolset. They can offer us the quickest way to detect running apps and services on remote open ports. And Masscan can be used for both defensive and offensive investigations.
Main features
- Scalable: Probably the most important feature of Masscan is its ability to transmit up to 10 million packets per second through its asynchronous architecture.
- Portability: The software can be compiled and run on all three major operating systems: Windows, MacOS and Linux.
- Banner checking: Apart from merely performing port scans, the tool can also complete TCP connections to fetch basic banner information.
- Nmap Compatibility: Masscan was developed with the goal of making the tool’s usage and output as similar to Nmap’s as possible. This enables users to translate their Nmap knowledge quickly.
Although there is a lot of Nmap compatibility, there are a couple of differences worth mentioning that separate Masscan from Nmap:
- There are no default ports to scan with Masscan
- Masscan only supports IP addresses and simple ranges (while Nmap supports DNS names too)
Who is Masscan for
Masscan is useful for red teamers doing offensive research (like penetration testing) as well as blue teamers and IT managers doing defensive research (like finding attack vectors within their network).
Masscan is also useful for both beginners and advanced users. It isn’t difficult to use and provides valuable functionality for researchers performing larger investigations.
Installation
Now we’ll cover Linux and MacOS installation procedure for Masscan.
Did you know that using a virtual server and a dedicated server to hack and test penetration in most data centers is not allowed and will cause the server to be blocked?
But what is the solution to this problem? You need a warez virtual or dedicated server to perform hacking, hacking, crack and test penetration.
We have solved this problem for you by providing Warez VPS and Warez Dedicated Server with the best quality.
Installing Masscan on Linux
The quickest way to install Masscan on Linux is to download the source code and compile the software. The tool may already exist in pentesting distros like Kali Linux, but we haven’t verified that.
It’s always important to use some type of sandboxing environment when installing new software. You could opt for a virtual machine (VM), container or a remote test server. We used Ubuntu 20.04 for this review and any commands used here should apply to Debian-based distros (and with a few minor tweaks, to other distros as well).
The first step is to install some necessary software:
sudo apt update
sudo apt upgrade
sudo apt install git gcc make libpcap-dev
Next we clone the official repo and compile the software:
git clone https://github.com/robertdavidgraham/masscan
cd masscan
make
You might get 1 or 2 warnings during the compilation, but if the software compiled successfully, you will see an output like:
Masscan examples
We’ll now attempt to run a few basic commands to see Masscan in action. Firewalls or proxies may block IPs that aggressively do port scans, and we’ll use this hindsight to run our tests.
Single IP port scan
Our first test is a single IP and single port scan of a malvertising IP we’re tracking.
./masscan 198.134.112.244 -p443
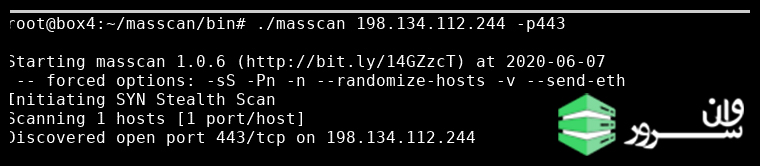
The tool confirmed that port 443 is indeed open at the chosen IP.
Advanced port scan against multiple ports
An advanced scan can be executed to analyze multiple ports or a range of ports on an IP subnet. We’ll share examples for both and the output for a multi-port analysis.
./masscan 198.134.112.240/28 -p80,443,25 #multiple ports
./masscan 198.134.112.240/28 -p1000-9999 #range of ports
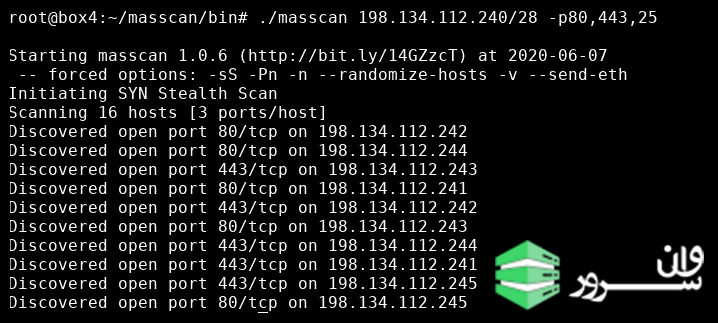
The scanner tells us how many hosts (16) were found, and then displays which ports are open on which IP addresses.
Scanning the top ports
This is another interesting feature: Masscan users can scan the most popular ports by using the ‘top-ports’ option from Nmap command with Masscan.
The syntax is simple, just add “–top-ports X”, replacing the X with a number of popular ports, for example 10 or 100, which are the most popular ones used by security researchers.
So the full syntax would look like:
masscan 192.168.1.105 ‐‐top-ports 10
This saves you time, as you’re focused on the most important ports from Nmap scan stats.
Scanning a subnet
Now let’s use Masscan to its full potential, by running a scan on a bigger subnet and at a faster rate, looking for the top 100 Nmap ports.
./masscan 198.134.112.0/20 --top-ports 100 --rate 100000 > output.txt
We piped the results of this scan to a file so that we could store the results of the scan. The results show that 4096 hosts were found, and among them we found a number of interesting details. Besides the usual ports of 80/443, some of the IP addresses had open ports such as: 21, 23, 53, 111, 427 and 514.
Exclude targets from your scan
Sometimes you need to reduce the number of hosts that are going to be scanned. In order to skip some of them, the ‘exclude targets’ option can be of help.
Masscan enables you to create an exclude file, so you can use the –excludefile parameter for any of your scans. The syntax would look like this:
masscan 192.168.1.105 ‐‐top-ports 10 ‐‐excludefile exclude-list.txt
Once you run the scan, a warning will be seen at the beginning of the scan:
exclude-list.txt: excluding 1 range from file
Scanning the entire Internet with Masscan
As we said before, Masscan was built with speed in mind. It’s prepared to run massive amounts of port scans across networks. Therefore, here you have a few examples of how to scan the entire Internet, for one specific port, or for all of the 65535 ports for each host.
How can I scan the Internet for one specific port
Just use this syntax, at full speed (10 million p/s)
masscan 0.0.0.0/0 -p22 --rate 10000000 #see footnote below [1]
This will trigger a massive scan across the whole internet, against port 22.
How can I scan the Internet for all the existing ports?
masscan 0.0.0.0/0 -p0-65535 --rate 10000000 #see footnote below [1]
Further tests
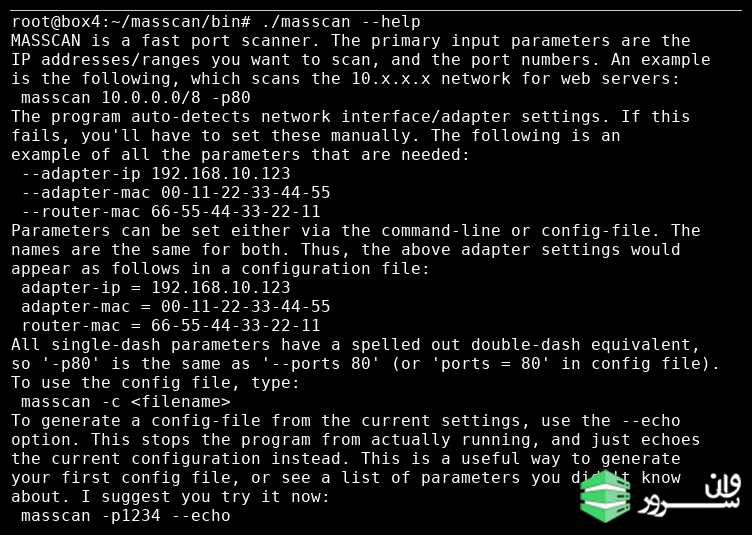
The –help command becomes handy to get a full picture of Masscan’s full potential, where you can find a wide range of options for advanced scanning techniques, as you see below:
Conclusion
Masscan is a great tool. It’s simple to install and quick and easy to use. Unlike other traditional port scanning solutions like Nmap, Masscan focuses on speed and accurate results with a great set of options, making it one of the best port scanners around.

















اولین نفر باشید که نظر ارسال میکنید